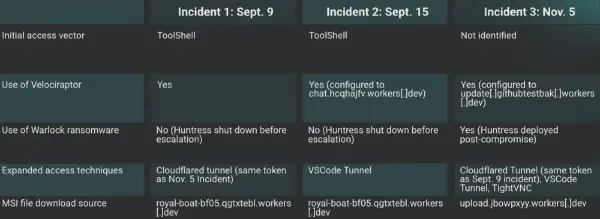
Investigation uncovered three distinct incidents where threat actors weaponized Velociraptor, a legitimate DFIR tool, for persistent command-and-control access. Attackers exploited SharePoint and WSUS vulnerabilities, installed Velociraptor as a Windows service communicating through Cloudflare tunnels, and deployed secondary tools including VS Code, OpenSSH, and TightVNC. One incident linked to Storm-2603 resulted in Warlock ransomware deployment.
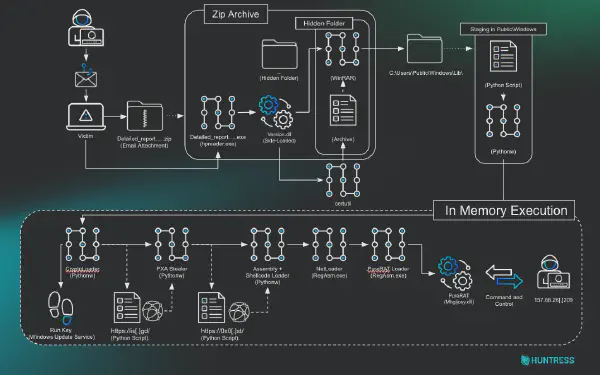
Vietnamese threat actor behind PXA Stealer has evolved their capabilities, deploying a sophisticated 10-stage attack chain culminating in PureRAT—a commercial .NET remote access trojan. The campaign demonstrates tactical maturity with DLL sideloading, multi-layer obfuscation, in-memory execution, and progression from credential theft to full system surveillance including hidden desktop access, webcam/microphone spying, and real-time keylogging.
Chinese-linked threat actors compromised over 100 systems across Taiwan, Japan, South Korea, and Hong Kong by weaponizing Nezha, an open-source monitoring tool, to deliver Gh0st RAT. The sophisticated attack chain exploited vulnerable phpMyAdmin panels using log poisoning techniques, deployed web shells via SQL injection, and used the Nezha agent for remote command execution before delivering the final payload.