Huntress - Weaponized Velociraptor Delivers Ransomware ↗ ↖
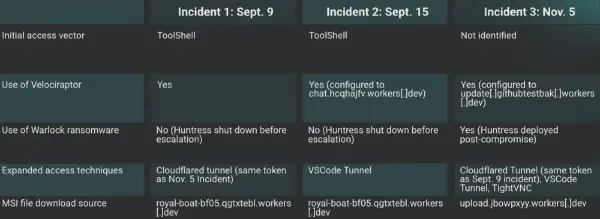
Investigation uncovered three distinct incidents where threat actors weaponized Velociraptor, a legitimate DFIR tool, for persistent command-and-control access. Attackers exploited SharePoint and WSUS vulnerabilities, installed Velociraptor as a Windows service communicating through Cloudflare tunnels, and deployed secondary tools including VS Code, OpenSSH, and TightVNC. One incident linked to Storm-2603 resulted in Warlock ransomware deployment.